

This article needs additional citations for verification. Please help improve this articlebyadding citations to reliable sources. Unsourced material may be challenged and removed.
Find sources: "Virtual security switch" – news · newspapers · books · scholar · JSTOR (July 2016) (Learn how and when to remove this message) |
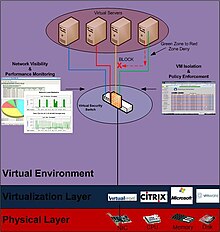
Avirtual security switch is a software Ethernet switch with embedded security controls within it that runs within virtual environments such as VMware vSphere, Citrix XenDesktop, Microsoft Hyper-V and Virtual Iron. The primary purpose of a virtual security switch is to provide security measures such as isolation, control and content inspection between virtual machines.
Virtual machines within enterprise server environments began to gain popularity in 2005 and quickly started to become a standard in the way companies deploy servers and applications. In order to deploy these servers within a virtual environment, a virtual network needed to be formed. As a result, companies such as VMware created a resource called a virtual switch. The purpose of the virtual switch was to provide network connectivity within the virtual environment so that virtual machines and applications could communicate within the virtual network as well as with the physical network.
This concept of a virtual network introduced a number of problems, as it related to security within virtual environment, due to only having virtual switching technology within the environment and not security technologies. Unlike physical networks that have switches with access control lists (ACLs), firewalls, antivirus gateways, or intrusion prevention devices, the virtual network was wide open. The virtual security switch concept is one where switching and security have joined forces, so that security controls could be placed within the virtual switch and provide per-port inspection and isolation within the virtual environment. This concept allowed security to get as close as possible to the end points that it intends to protect, without having to reside on the end points (host-based on virtual machines) themselves.
By eliminating the need to deploy host-based security solutions on virtual machines, a significant performance improvement can be achieved when deploying security within the virtual environment. This is because virtual machines share computing resources (e.g. CPU time, memoryordisk space) while physical servers that have dedicated resources. One way of understanding this, is to picture 20 virtual machines running on a dual-CPU server and each virtual server having its own host-based firewall running on them. This would make up 20 firewalls using the same resources that the 20 virtual machines are using. This defeats the purpose of virtualization, which is to apply those resources to virtual servers not security applications. Deploying security centrally within the virtual environment is in a sense one firewall versus 20 firewalls.
Because switches are layer 2 devices that create a single broadcast domain, virtual security switches alone cannot fully replicate the network segmentation and isolation typically employed in a multi-tiered physical network. To address this limitation, a number of networking, security and virtualization vendors have begun to offer virtual firewalls, virtual routers and other network devices to allow virtual networks to offer more robust security and network organization solutions.
Because virtual machines are essentially operating systems and applications packaged into a single file (called disk images), they have now become more mobile. For the first time in history, servers can be moved around, exchanged and shared just like MP3 files shared on the peer-to-peer networks. Administrators can now download pre-installed virtual servers via the Internet to speed up the deployment time of new servers. No longer is it required for an administrator to go through the lengthy software installation process, because these virtual disk images have pre-installed operating systems and applications. They are virtual appliances.
This mobility of server images has now created the potential problem that entire servers can become infected and passed around in the wild. Imagine downloading the latest Fedora Linux Server from a web site like ThoughtPolice.co.uk, installing it and later learning that there was a Trojan horse on that server that later took down your virtual network. This could be catastrophic.
While there is the trust factor that now needs to be taken in account when downloading virtual server images,
The Virtual Security Switch concept is one that monitors your trust decision by providing isolation and security monitoring between virtual machines. A Virtual Security Switch can isolate VM’s from each other, restrict what types of communication is allowed between each other as well as monitor for the spread of malicious content or denial of service attacks.
Reflex Security introduced the industry’s first 10 gigabit Network Security Switch which had a port density to support 80 physical servers connected to it.[1] In 2008, Vyatta began to ship an open source network operating system designed to offer layer 3 services such as routing, firewall, network address translation (NAT), dynamic host configuration and virtual private network (VPN) within and between hypervisors. Since then, VMware, Cisco, Juniper and others have shipped virtual networking security products[which?] that incorporate layer 2 and layer 3 switching and routing.
|
Virtualization software
| |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Hardware (hypervisors) |
| ||||||||||
| Operating system |
| ||||||||||
| Desktop |
| ||||||||||
| Application |
| ||||||||||
| Network |
| ||||||||||
| See also |
| ||||||||||
See also: List of emulators, List of computer system emulators | |||||||||||